Shared Security: Ripping off the Masks
Web3 scalability is swiftly progressing, and a crucial element of this evolution lies in the security model that undergirds decentralized networks. In September 2022, Ethereum underwent ‘The Merge’ — which marked the shift of its underlying security model from Proof-of-Work(PoW) toProof-of-Stake(PoS).
Introduction
Web3 scalability is swiftly progressing, and a crucial element of this evolution lies in the security model that undergirds decentralized networks. In September 2022, Ethereum underwent ‘The Merge’ — which marked the shift of its underlying security model from Proof-of-Work (PoW) to Proof-of-Stake (PoS). The implications of The Merge are multifaceted. First, it lends further legitimacy to PoS as a security model — PoS consensus secures hundreds of billions of dollars of value across multiple networks, Ethereum being the largest. Second, it paves the way for the creation of new protocols that take advantage of the underlying architecture of PoS.
One of the major advantages of PoS is that locked or staked collateral is reusable for multiple purposes. In this post, we’ll give a general overview of how PoS systems work and show how ‘shared security’ modules can be developed on top of PoS that leverages the financial collateral that is locked within the network. We’ll then discuss the three leading shared security models in the market today: Interchain Security (ICS), Eigenlayer and Mesh Security. Interchain Security is a product for Cosmos chains to provide security to new chains by leveraging their existing validator set. It is currently used by the Cosmos Hub and Saga. Eigenlayer is a shared solution for Ethereum which enables Eth validators to offer Additional Validator Services (AVS) to secure new trust networks related to Ethereum’s roadmap. Lastly, we’ll delve into Mesh Security, a network-based approach that connects multiple PoS chains to increase economic security across a multitude of chains that has been analogized to the NATO alliance.
In comparing the advantages and disadvantages of these shared security models, it is vital to acknowledge that no single solution fits all scenarios. Each shared security approach has its unique strengths and weaknesses, and implementation details are driven by the underlying network design and requirements. By understanding the various shared security models and the intricacies of their designs, we hope to shed light on the importance of customizing shared security solutions to address the diverse needs of the ever-growing Web3 ecosystem.
What’s So Great about Proof-of-Stake?
To appreciate the advantages of PoS, the consensus algorithm employed by most blockchain networks, it is instructive to briefly examine PoW, the fundamental consensus model that safeguards Bitcoin. PoW is safeguarded by the hash power contributed by miners. In this model, miners compete to solve complex mathematical problems, and the first one to solve the problem gets to add a new block to the blockchain and receives a reward that is paid in $BTC for their efforts. Solving these complex mathematical problems requires hash power: a measure of the computational power. A new block is considered to be valid and accepted by the network when miners begin to build blocks on top of the block that was just created. To corrupt the network, an adversary would need to command the majority of the network’s hash power. To acquire such hash power, an attacker would need to spend billions acquiring the proper hardware, related infrastructure and millions of dollars per hour to continuously attack the network. Some estimate that it would cost an attacker more than $5 billion to effectively attack the network.
The energy consumption of the Bitcoin network as measured by hash power is both a feature and bug. While its current energy consumption makes it extremely difficult (if not impossible) to be corrupted by an external party, its energy consumption makes it potentially problematic to the environment. In addition, PoW cannot be scaled to secure multiple chains. Since hash power is required to validate a single block on a single chain, diverting some of that hash power to a second PoW chain effectively reduces the security of both chains. PoS, however, presents a solution to secure high-value networks without the ensuing environmental concerns and can be scaled to secure multiple chains.
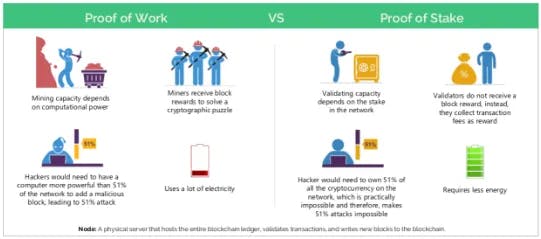
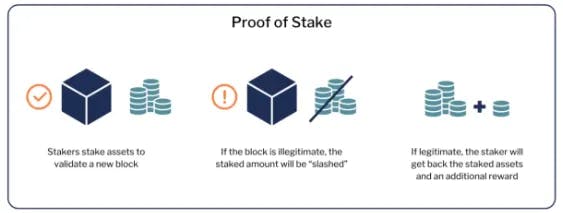
PoS, a consensus algorithm, secures a blockchain network by locking financial collateral rather than utilizing hash power, typically in the form of the network’s native cryptocurrency. The main entities involved in a PoS system are validators and stakers (also known as delegators). Whereas miners compete with each other to solve complicated cryptographic puzzles in a PoW network, validators are pre-selected in PoS network based on the amount of locked financial capital (staked collateral) they accrue; more staked collateral leads to a higher chance to validate the next block.
To incentivize honest and non-malicious behavior within the network, PoS relies on a mechanism called slashing. Slashing is a penalty mechanism where validators lose a portion of their staked collateral pledged to their node if they are found to be engaging in malicious activities or failing to fulfill their obligations to the network. Different slashing conditions can exist depending on the PoS implementation, but common ones include double-signing or downtime. The nuances of the specific slashing conditions can be tailored to the specific blockchain network and its specific use case.
Slashing constitutes one of the three critical components of a PoS network. The other two components involve 1) locking up financial collateral to validators and 2) validators receiving rewards as they fulfill their obligations on the network, such as creating a new block or attesting to the validity of blocks produced by others.
Armed with this understanding of PoS, let’s investigate the concept of shared security more thoroughly, enabling us to examine the leading shared security protocols in subsequent sections.
What is Shared Security?
Shared security leverages the staked collateral that is locked with a validator and utilizes it for other purposes. In other words, validators can rehypothecate their financial stake by signing up for extra slashing risks in return for the additional financial return that is related to the new services that a validator might offer. The idea builds upon the three main components of PoS: locking collateral, signing up for obligations and signing up for slashing risks. In the context of shared security, the financial collateral that is already locked within a PoS system can be reused to secure multiple networks, provided that validators and their delegators are willing to accept additional obligations and risks.
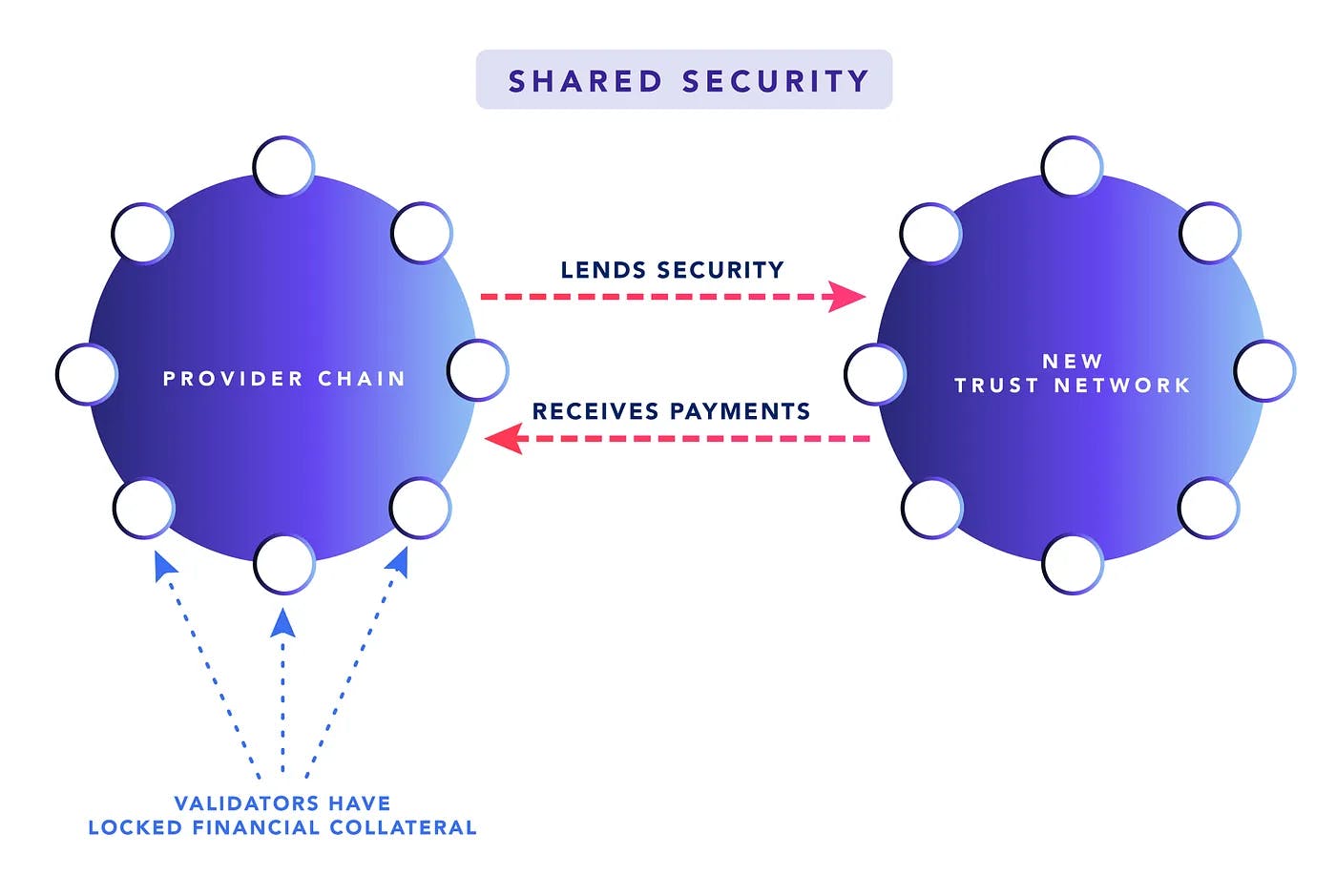
Economic Flywheels
Shared security modules can create a virtuous economic flywheel for blockchain networks. As validators share the underlying security to a new trust network, they receive payments for the service that they provide. This payment is then shared with delgators, which increases the financial return on the locked capital that provides the underlying economic security. The increased financial return on locked capital improves the value proposition for locking tokens with validators, which can lead to higher economic security for the blockchain network. The higher economic security leads to a more attractive value proposition for new trust networks that want to be secured by a higher amount of economic security. The flywheel can be demonstrated below:
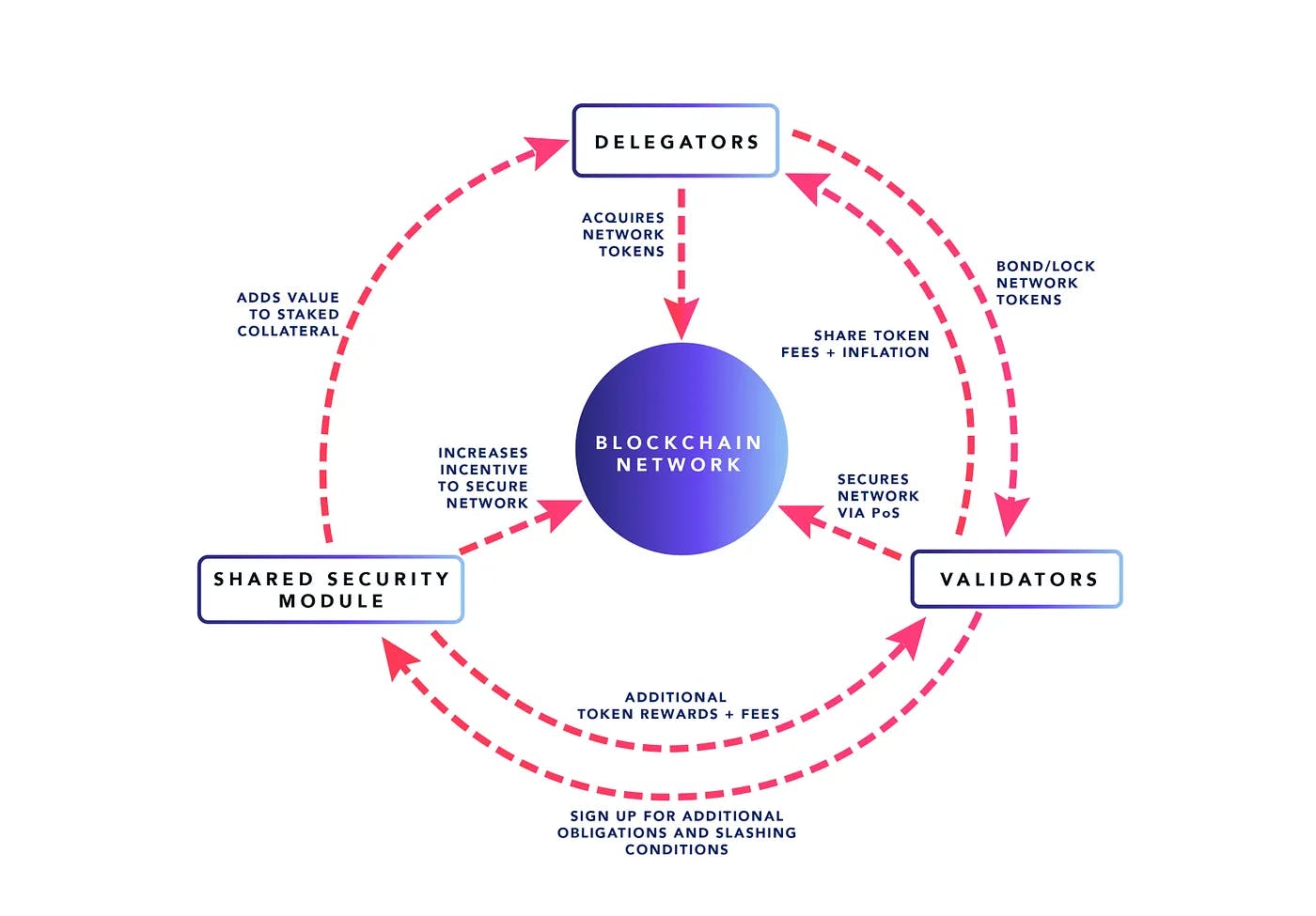
Pros and Cons of Shared Security
Shared security modules represent a significant innovation for the entirety of Web3, as they facilitate the bootstrapping of new trust networks. In the absence of shared security, new networks must navigate the arduous process of designing a staking token, incentivizing validators, recruiting investors, generating sufficient interest via marketing, all with the aim of establishing a network with high economic security. For new networks or novel blockchain applications, shared security allows teams to bootstrap a high level of economic security and generate incentive alignment with a particular ecosystem. A set of individuals interested in launching a new trust network or a blockchain application can simply bootstrap that network by relying on existing infrastructure and validator sets. Conversely for stakers, shared security gives additional utility to locked assets, ultimately increasing the utility of the token (and increasing security at the same time).
The major drawback of shared security is that the security implications for the chain providing security are not yet completely understood, nor have they been rigorously tested in a live production environment. While shared security modules can allow for new trust networks to be bootstrapped from existing economic security, it is possible that shared security can actually decrease the economic security of the providing chain.
The notion of shared security initially emerged from the Interchain foundation, an organization that is a trailblazer in innovation and research pertaining to PoS systems. After years of development, the first implementation of shared security, known as interchain security, has been shipped to the Cosmos Hub, with many projects eager to utilize interchain security to bootstrap economic security and incentive alignment. Shared security is now coming to the Ethereum ecosystem via Eigenlayer with the promise to further decentralize the Ethereum tech stack and add value to $Eth, the capital asset. Mesh security promises to increase economic security and economic alignment across the Cosmos ecosystem. In the subsequent sections of this essay, we will scrutinize these shared security mechanisms, discuss their advantages and disadvantages, and offer insights into the practical aspects of shared security and its potential to influence the future trajectory of Web3.
ICS — Saga and the Cosmos Hub
How is Security Offered?
ICS is a module that is built within the Cosmos tech stack, which is powered primarily by Tendermint consensus, a Byzantine Fault Tolerant (BFT) consensus algorithm where a limited number of validators (typically anywhere from 20–200 validators) are responsible for validating a blockchain network and the applications that sit on top of it.
ICS v1 allows validators on Cosmos networks to sign up for additional slashing conditions in exchange for validating new blockchain networks. Validators create a second node to support the new blockchain, and the identity of the new node is correlated to the identity on the original (parent) chain. If the validator node on the new (child) chain misbehaves, the misbehavior is relayed back to the parent chain via a blockchain messaging solution known as Inter-Blockchain Communication (IBC). Such misbehavior may lead to slashing of the staked collateral on the parent chain. IBC plays a crucial role in relaying validator behavior from a consumer chain to the provider chain, ensuring transparency and accountability across interconnected networks. It is a protocol that facilitates communication between different blockchains, allowing these chains to exchange information like tokens, data and validator actions. The IBC protocol is a critical component of the Cosmos ecosystem and plays a crucial role for interchain security.
How is Payment Offered?
ICS v1 is currently being deployed on the Cosmos Hub and Saga, each with their own unique payment channels. For instance, the Stride network recently announced its plan to become a child chain of the Cosmos Hub. Stride’s core product provides liquidity to staked assets, such as staked $ATOM. By transitioning from a standalone chain to a child chain for the Cosmos Hub, they can quicken interest in their liquid staking solution and benefit from greater economic security; the Stride network currently has approximately $35MM of economic security but will have over $2BB of economic security when it transitions to becoming a child chain for the Cosmos Hub. The Cosmos Hub benefits from increased liquidity that the Stride liquid staking module delivers, making such a strategic move a win-win for both networks.
In exchange for the economic security inherited from the parent chain, Stride intends to create a strong economic synergy with the Cosmos Hub validator and delegators. A child chain will typically pay delegators on the parent chain in some form of token incentive, such as transaction fees, captured MEV, inflationary rewards or other mechanisms. For Stride, they intend to share various revenues with the Cosmos Hub, including up to 15% of liquid staking rewards, 15% of inflationary staking rewards and 15% of MEV and transaction fees.
From a validator and delegator perspective, securing a child chain via ICS is economically viable and desirable if the external rewards from the child chain are worth the risk of the extra slashing conditions that are imposed. In the case of the Cosmos Hub, delegators and stakers assess these risks and returns through voting on governance proposals. Cosmos Hub’s governance-gated ICS offers significant flexibility in payment structures at the cost of a slow, permissioned deployment process. If a child chain does not have an attractive value accrual mechanism to pay the Cosmos Hub, they won’t be able to convince Cosmos governance to provide security.
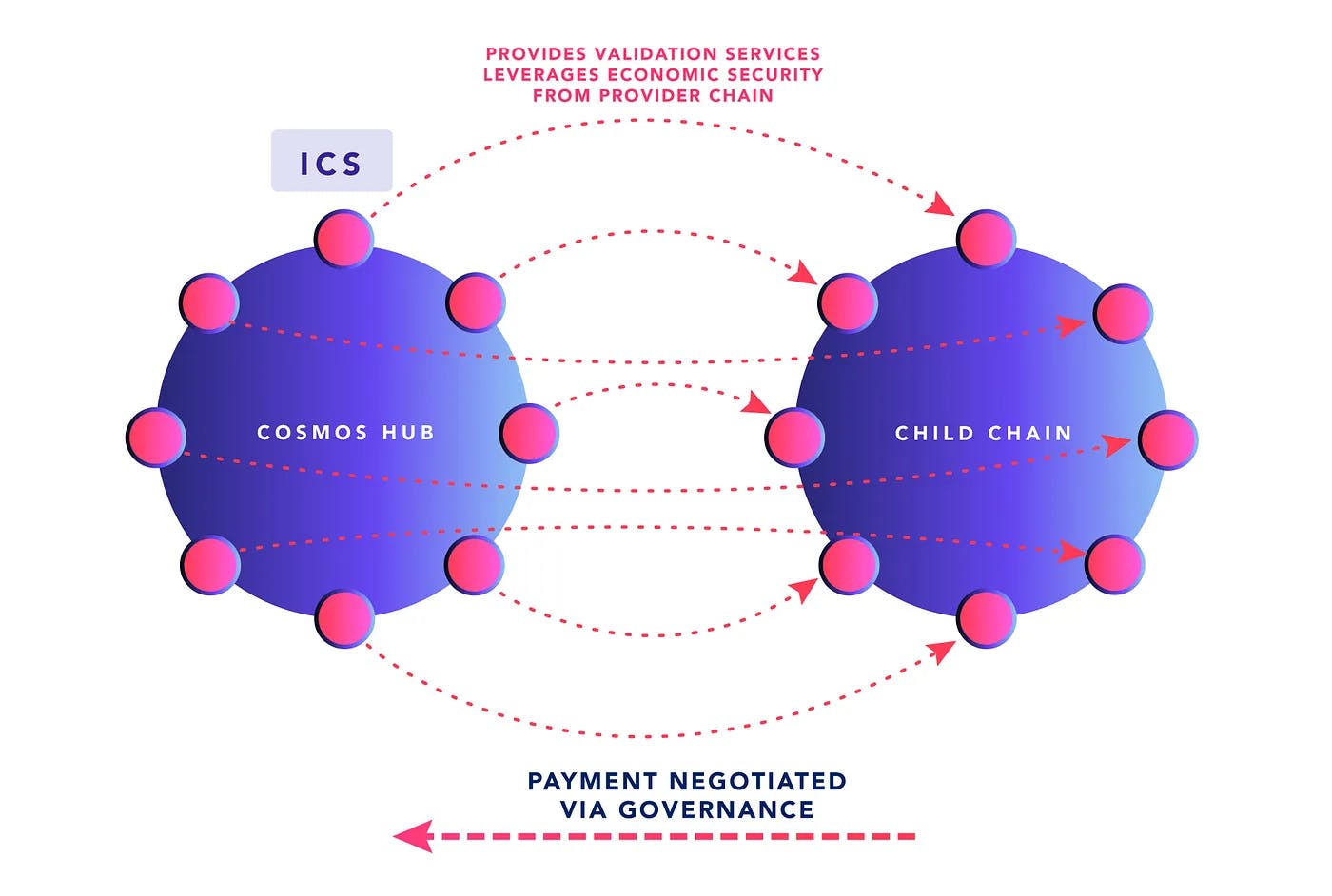
For Saga, an auction mechanism ensures that validators are properly compensated for the risk of validating a new network, regardless of the value accrual on that network. The auction mechanism is a part of Saga’s novel token economic model where the price for provisioning a blockchain network is known ahead of time. Saga offers significant flexibility through a permissionless deployment process, at the cost of a homogenized payment structure. Teams looking to utilize ICS simply need to decide whether this price of running a chainlet is worth the benefits, knowing that validators for the Saga ecosystem will guarantee interchain security at that price. For more details, check out Saga’s Token Mechanism and Incentive Paper.
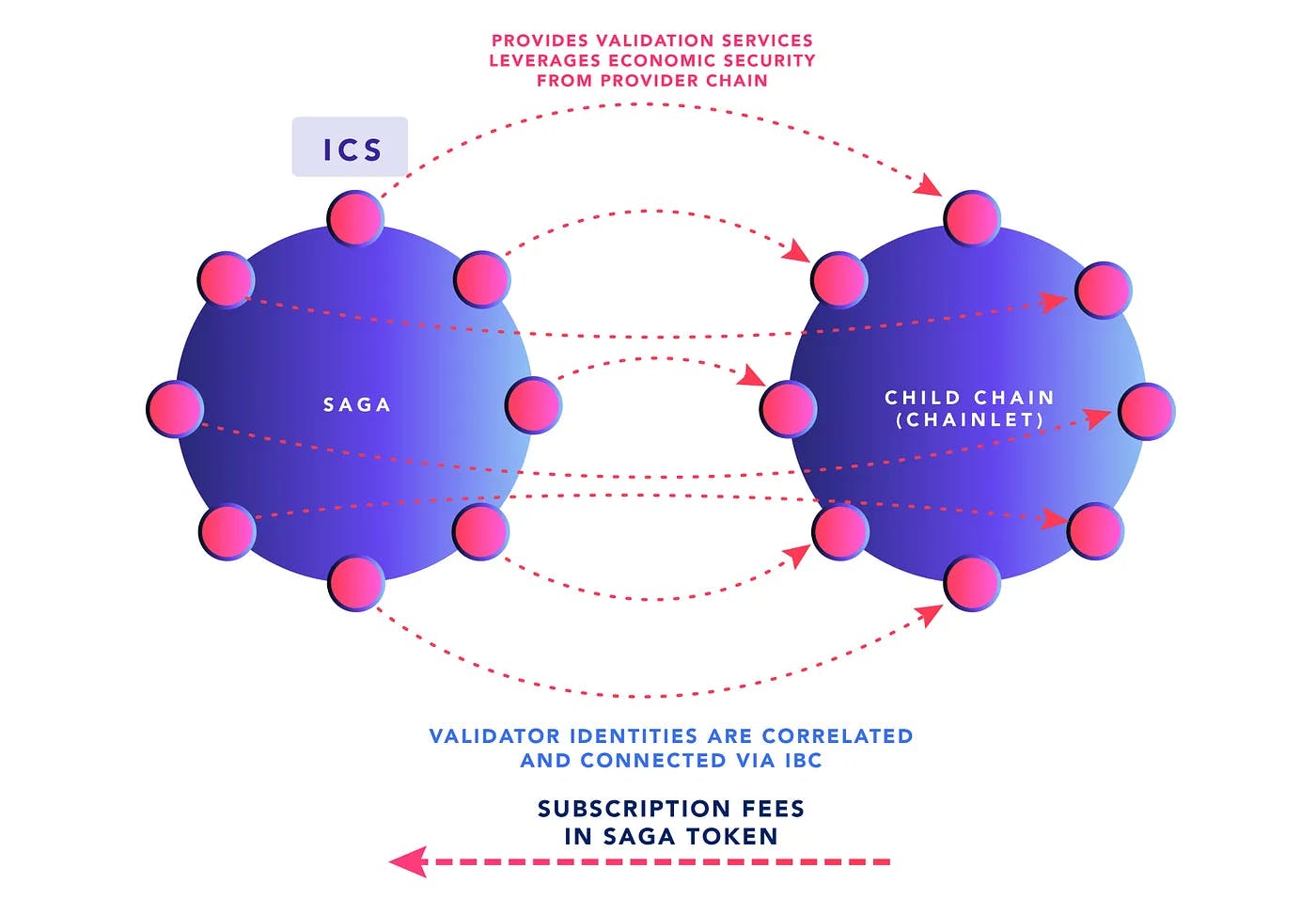
Regardless of whether the mechanism for interchain security is gated by governance or a permissionless version as developed by Saga, ICS can bring economic value to staked tokens, driving the economic flywheel for both projects.
Pros and Cons
The main benefit of ICS is that it allows a new network to bootstrap a high level of economic security without going through the lengthy process of designing a staking token and recruiting validators. So long as a governance proposal is passed or a fee deposit is submitted, the new network will inherit all the validators and the resulting economic security from the parent chain.
While networks that are utilizing interchain security can inherit the full economic security of the provider chain, it comes at the cost of the sovereignty of the individual validators on the provider chain. ICS v1 forces validators of the parent chain to validate a new network regardless of their desire or interest in validating the new network: validators must validate a new network on the Cosmos Hub if a governance proposal passes or if a fee deposit is paid on the Saga network. It doesn’t matter if a validator or delegator is uncomfortable with the additional slashing conditions. That said, future versions of ICS (i.e. version 2 and version 3), will have opt-out options for validators, but those versions are still very much in research and development.
This opt-out feature is one of the points of distinction between ICS and Eigenlayer. Eigenlayer is one the leading shared security solutions in the Ethereum ecosystem today, and its architecture allows for Ethereum validators to preserve their sovereignty while also adding value to the staked $ETH collateral.
EigenLayer Restaking for Ethereum
EigenLayer constitutes a shared security solution specifically developed for the Ethereum ecosystem, adhering to the tradeoffs inherent in the Ethereum’s PoS system. For a detailed overview of the distinctions between Ethereum PoS and Tendermint, click here.
How is Security Offered?
LSTs — “Liquid Staking Tokens” are an important part of Eigenlayer’s shared security implementation. The value of an LST typically tracks the value of the underlying staked collateral and accumulated rewards. For example Lido — a liquid staking provider similar to Stride — has spun up thousands of validator nodes for the Ethereum ecosystem and the value generated from these nodes is captured by the $stETH token. Lido’s $stETH can be used in various DeFi applications, such as lending platforms, decentralized exchanges and yield farming strategies. This allows users to rehypothecate their $stETH in DeFi while still contributing to the security of the Ethereum network.
While LSTs can bring liquidity to staked collateral and be utilized in DeFi, it doesn’t drive additional value to the underlying staked collateral. Eigenlayer is a framework that enables staked capital on Ethereum to be rehypothecated to allow validators to offer additional services, known as Active Validator Services (AVS). This rehypothecation occurs when an LST is locked up in an Eigenlayer smart contract, or when the validator directs their withdrawal access to the same Eigenlayer smart contract. By doing so, the staked capital can be slashed via this smart contract should a validator misbehave when offering AVS.
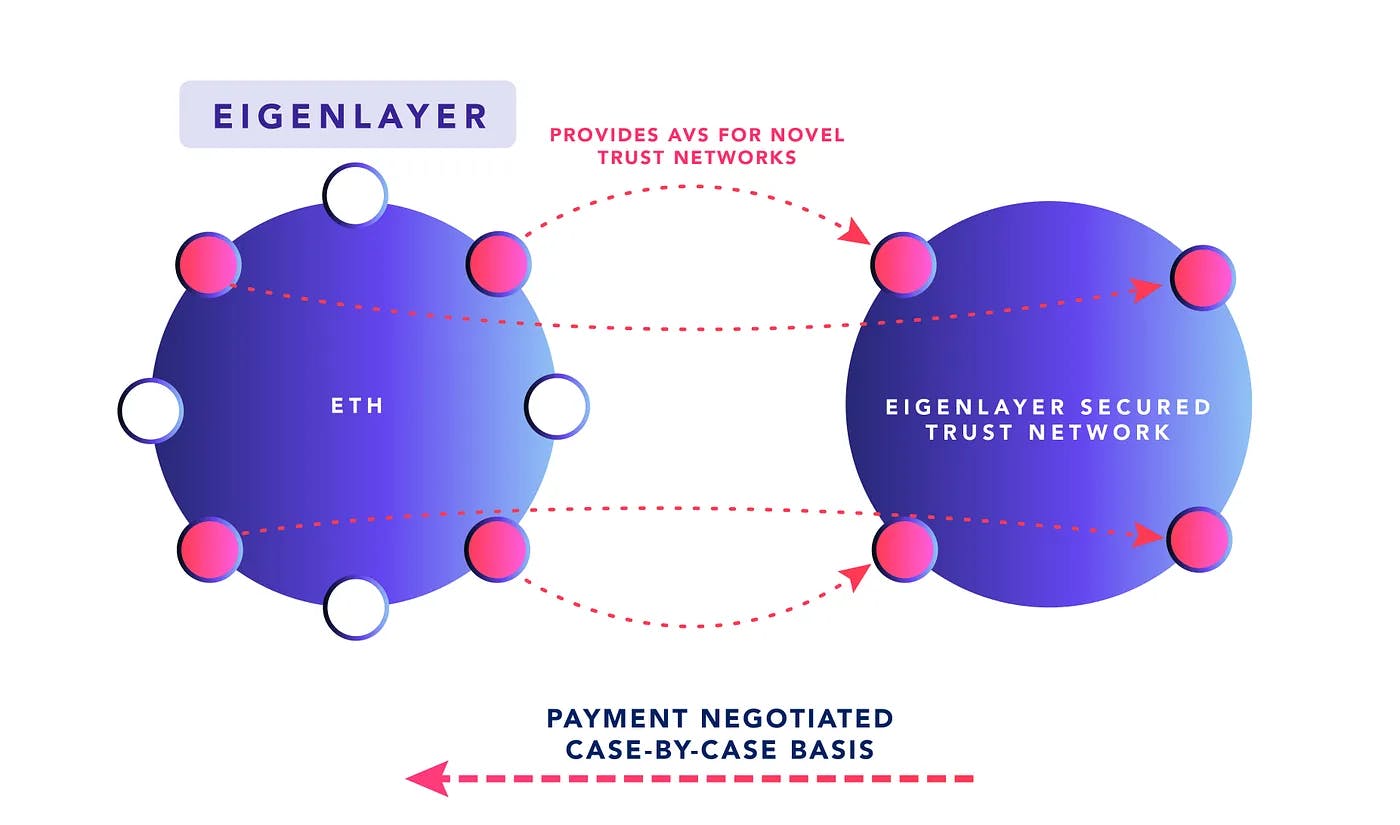
How is Payment Offered?
Examples of active validator services that could be offered via Eigenlayer include any kind of service that may require storage or computation and necessitates a high level of economic security. This is particularly useful for the creation of new decentralized trust networks, such as blockchains with novel designs, data availability layers, securing light-node bridges, providing oracle services, decentralized sequencers, fast-mode bridges for roll-ups, settlement chains with ultra-low latency or managing MEV (Minter Extractable Value) to name a few. The breadth of AVS is still being explored, but safe to say the list will likely grow over time.
Similar to ICS within Cosmos, these extra slashing conditions that are inherent to Eigenlayer’s design also come with additional financial rewards. For example, an Ethereum validator could, in theory, offer decentralized sequencing services for many of the rollup solutions being deployed on Ethereum, like Arbitrum or Optimism. This would require a validator to direct their deposit address (or LSTs) to the Eigenlayer smart contract and spin up a new node to offer sequencing services. These Ethereum validators could receive $ARB or $OP tokens in exchange for providing sequencing services. This type of economic relationship helps to decentralize a key component of the Ethereum tech stack (the execution layer) while also driving value to staked $ETH collateral. Eigenlayer unlocks a similar economic flywheel for Ethereum as ICS does for Saga and the Cosmos Hub.
Pros and Cons
The major benefit of EigenLayer is that it serves as an experimental playground for future Ethereum upgrades, allowing developers to test new features and improvements in a live but controlled environment. Eigenlayer also preserves sovereignty for an Ethereum validator; an individual validator can choose to NOT opt-in to the services that Eigenlayer can offer and just validate the Ethereum network, preserving their control over the services that they choose to offer. This is an important feature of Eigenlayer’s design, as forced inclusion into Eigenlayer could negatively impact the security of the entire Ethereum network.
While the opt-out feature comes as a benefit to Ethereum validators, it does make it harder to bootstrap economic security for new trust networks: they must work to individually recruit validators and stake, which can be a time-consuming process. In addition, the security of a subset of Ethereum validators may be only a small fraction of the entire economic security that Ethereum can offer.
Similar to ICS, Eigenlayer correlates the identity of a validator to a new node that can offer additional services. But what about two validator nodes that exist on two separate networks? Can validator stake be correlated in any way that produces stronger economic security? Enter mesh security.
Mesh Security for the Interchain
How is Security Offered?
The concept of mesh security was popularized by Sunny Agarwal, one of the co-founders of Osmosis — the premier liquidity hub for the Interchain. He presented the idea for Cosmos chains to share security with each other, thereby increasing the economic security of both chains. Mesh security is a concept that applies to the Interchain (the blockchain networks that are connected to each other via IBC) and is specific to the Cosmos tech stack. What is noteworthy about the Interchain is that despite being a collection of independent chains, there is often a large overlap in validator sets for any particular chain. Consider Chorus One — a validator collective that currently runs 23 nodes across the Cosmos ecosystem, including nodes for the Cosmos Hub, Osmosis and eventually Saga. Sunny estimates that there is approximately a 70% overlap in validator sets for different networks in the interchain. This overlap is the foundation for mesh security to be implemented.
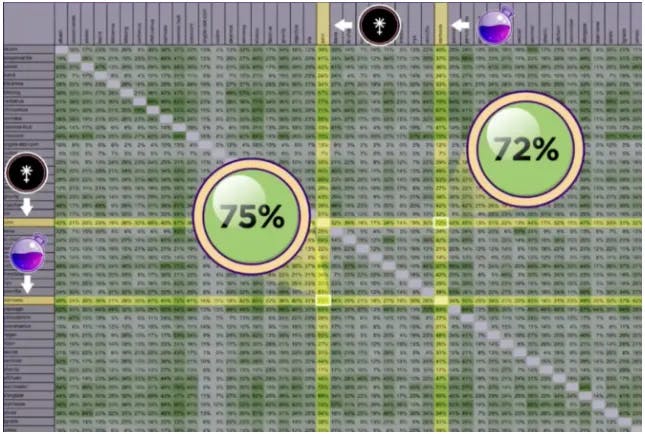
While a validator collective like Chorus One may run multiple nodes across the interchain, each of these nodes are tied to independent slashing conditions and staking rewards; the Chorus One validator on Osmosis validates blocks for the Osmosis chain and receives staking rewards in $OSMO whereas the Chorus One validator on the Cosmos Hub validates for the Cosmos network and receives staking rewards in $ATOM. What if the slashing conditions on these ‘independent’ nodes were tied to each other? In other words, if the Chorus One validator on Osmosis misbehaves, the Chorus One validator on Cosmos Hub can be slashed. Vice-versa, if the Chorus One validator on the Cosmos Hub misbehaves, the stake on the Chorus One validator can be slashed.
Why is this useful? Since the stake on the Chorus One validator on the Cosmos Hub can be slashed for misbehavior on the Osmosis chain, the economic security of the Chorus One validator is the total staked collateral on BOTH chains. The reverse is also true — the Chorus one validator on Cosmos Hub inherits security from the Chorus One validator on Osmosis.
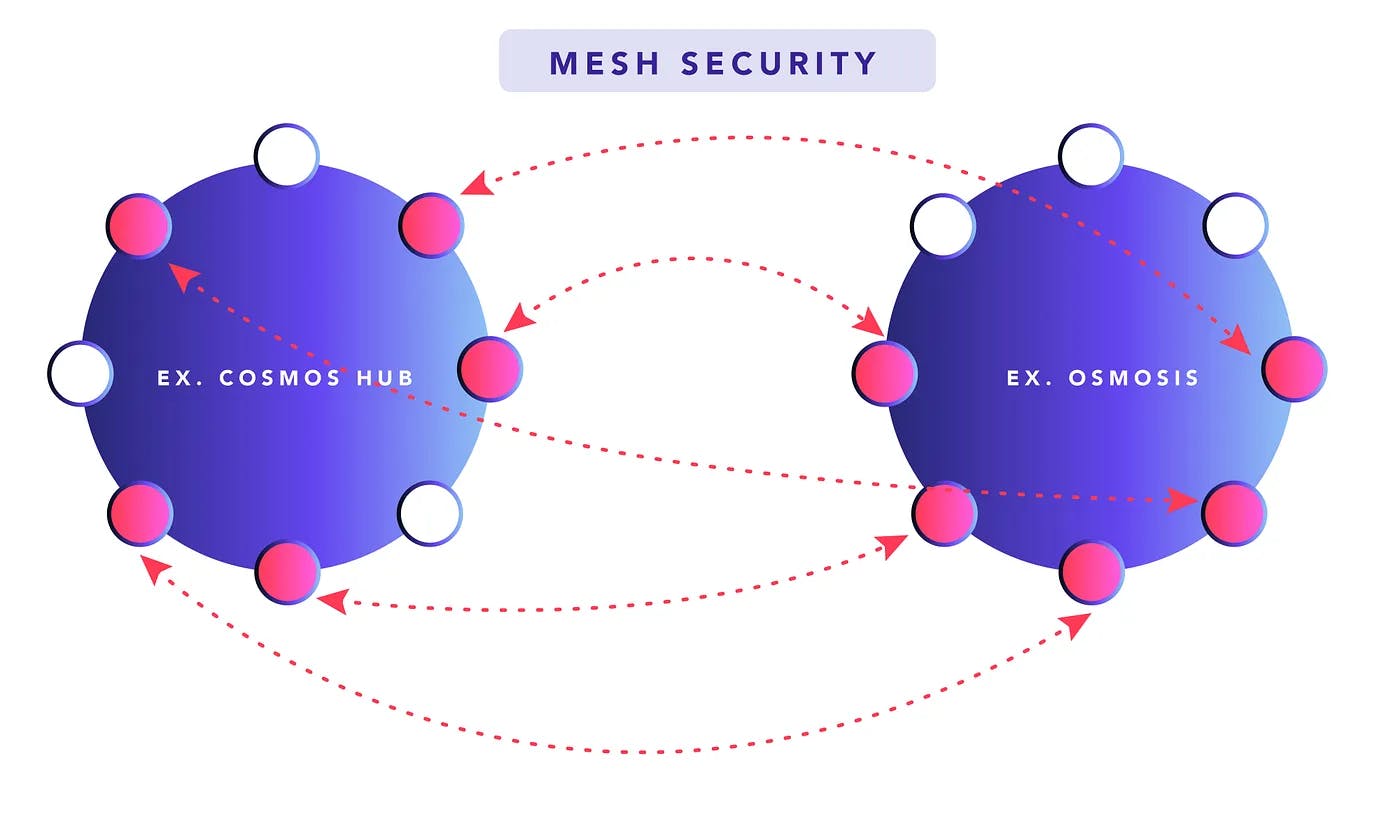
How is Payment Offered?
The other implication of tying slashing conditions across multiple chains is that staking rewards from one chain can now be shared with the node on the other chain. So a delegator who bonds $ATOM on the Cosmos Hub to the Chorus One validator can receive staking rewards in $ATOM and $OSMO, and the same applies for those who delegate $OSMO to the Chorus One validator on Osmosis. Similar to ICS, the messaging of slashing conditions and sharing of staking rewards is done via IBC.
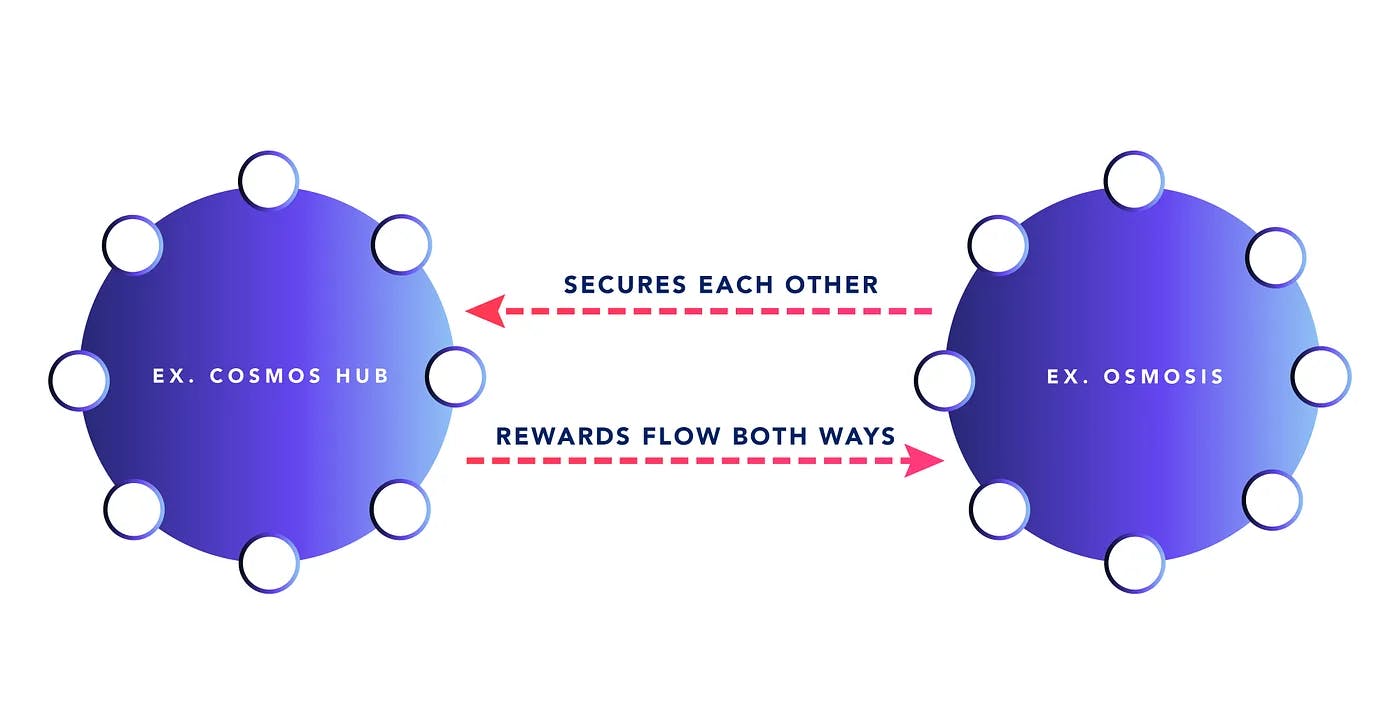
Mesh security is different from Eigenlayer and Interchain security in the sense that payments for increased security flow in both directions, instead of just one direction. The chains are helping to secure each other. In this sense, the NATO analogy is potentially an apt one.
Pros and Cons
Mesh security is an ideal solution for chains that are of similar market capitalizations and have an overlap in validator sets. It can be a great way for validators who run nodes on multiple networks to attract stake to their nodes by the sharing of rewards. In addition, mesh security makes sense for chains that already have strong existing relationships with each other, like Axelar and Osmosis: much of the value that exists on Osmosis today comes from wrapped assets that are secured via Axelar.
Unlike ICS and Eigenlayer, mesh security does not solve problems related to how to bootstrap security for new trust networks; it is a boutique solution for chains that already have some level of economic security and would like to increase it along with other chains. Mesh security may not be ideal for networks that are of dissimilar sizes relative to their market capitalization. Going back to the Chorus One example, the amount of value staked on the Chorus One validator on the Cosmos Hub is close to $40MM, whereas on Osmosis, the staked collateral is currently around $13MM. As previously mentioned, the total amount of economic security on the Cosmos Hub is over $2BB, whereas the economic security for Osmosis is currently less than $300MM. Delegators who stake on the Chorus One node on Cosmos may determine that the additional economic security from participating in mesh security may not be worth the additional slashing conditions, given the smaller size of the Osmosis chain. In addition, validators need to decide how rewards get distributed between their two nodes, and there are currently no best practices on how to design such a distribution.
Conclusion
As Web3 continues to proliferate, the economic security of blockchain networks will continue to grow by multiples. Shared security allows for new trust networks to be created, and for unique economic flywheels that can generate value for delegators, stakers, blockchain applications and users. Shared security is a vital innovation in the blockchain ecosystem, providing new opportunities for trust networks, increasing economic security and facilitating the growth of novel blockchain projects. Through various implementations such as Interchain Security, Eigenlayer, and Mesh Security, shared security allows validators to leverage their financial collateral to create additional value and generate higher returns on locked assets. While each of these implementations have their strengths and weaknesses, they all contribute to the overall robustness and adaptability of their respective ecosystems.